FAIR WARNING: Virtual Private Networks or VPNs might be illegal on your country.
On some countries like as Turkey, China, and Iran are blocking Facebook, Twitter, and
YouTube and if you are in any of this countries, you may not be able to access your
favorite sites. The only way to unblock them is by using VPN. For this Tutorial I
recommend using Easy VPN.
NOTE: Some VPN apps gives free Internet access but not for this tutorial.
Easy VPN installed!
Open Easy VPN and choose the country of your choice or press connect right away. The VPN will fake your device location. You can now enjoy your favorite apps and sites.
What is VPN and how does it work?
Here’s the complete explanation:
Source: https://gizmodo.com/5990192/vpns-what-they-do-how-they-work-and-whyyoure-dumb-for-not-using-one
For as ubiquitous as connectivity has become and how reliant we've grown on it, the
Internet is still a digital jungle where hackers easily steal sensitive information from the
ill-equipped and where the iron-fisted tactics of totalitarian regimes bent on controlling
what their subjects can access are common. So instead of mucking around in public
networks, just avoid them. Use a VPN instead. Between Wi-Fi spoofing, Honeypot
attacks, and Fire sheep, public networks really are cesspools. But if you're working
remotely and need to access sensitive data on your company's private servers, doing so
from an unsecured public network like a coffee shop Wi-Fi hotspot could put that data,
your company's business, and your job at stake.
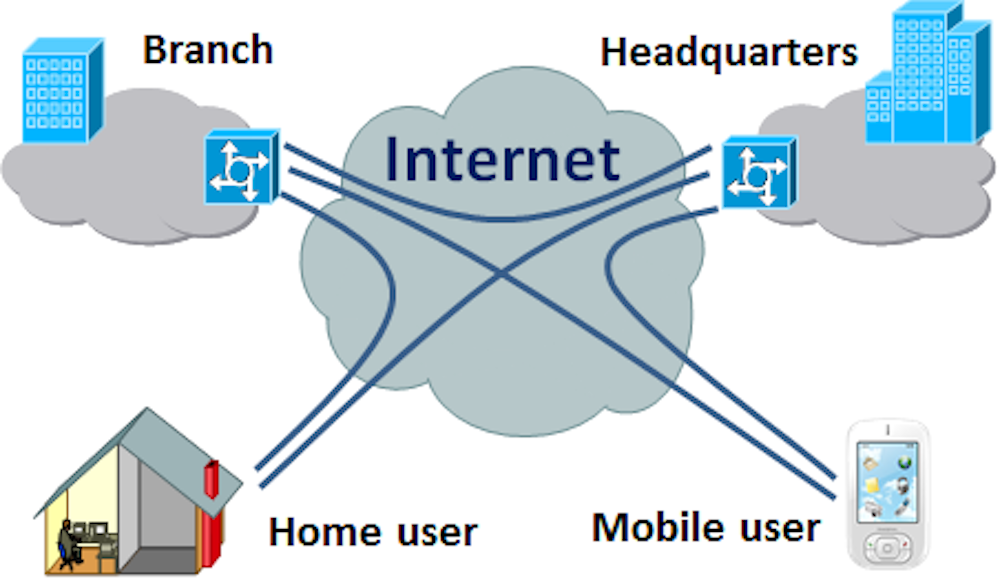
VPNs, or Virtual Private Networks, allow users to securely access a private network and
share data remotely through public networks. Much like a firewall protects your data on
your computer, VPNs protect it online. And while a VPN is technically a WAN (Wide Area Network), the front end retains the same functionality, security, and appearance as
it would on the private network.
For this reason, VPNs are hugely popular with corporations as a means of securing
sensitive data when connecting remote data centers. These networks are also becoming
increasingly common among individual users—and not just torrenters. Because VPNs
use a combination of dedicated connections and encryption protocols to generate virtual
P2P connections, even if snoopers did manage to siphon off some of the transmitted data,
they'd be unable to access it on account of the encryption. What's more, VPNs allow
individuals to spoof their physical location—the user's actual IP address is replaced by
VPN provider—allowing them to bypass content filters. So, you may live in Tehran but
appear to live in Texas, enabling you to slip past the government filters and commit the
treasonous act of watching a YouTube video. The horror
Establishing one of these secure connections—say you want to log into your private
corporate network remotely—is surprisingly easy. The user first connects to the public
internet through an ISP, and then initiates a VPN connection with the company VPN
server using client software. And that's it! The client software on the server establishes
the secure connection, grants the remote user access to the internal network and—
Bing, bang, boom—you're up to your elbows in TPS reports. The horror.
Many security protocols have been developed as VPNs, each offering differing levels of
security and features. Among the more common are:
- IP security (IPsec): IPsec is often used to secure Internet communications and
can operate in two modes. Transport mode only encrypts the data packet
message itself while Tunneling mode encrypts the entire data packet. This
protocol can also be used in tandem with other protocols to increase their
combined level of security.
- Layer 2 Tunneling Protocol (L2TP)/IPsec: The L2TP and IPsec protocols
combine their best individual features to create a highly secure VPN client.
Since L2TP isn't capable of encryption, it instead generates the tunnel while the
IPsec protocol handles encryption, channel security, and data integrity checks to
ensure all of the packets have arrived and that the channel has not been
compromised.
- Secure Sockets Layer (SSL) and Transport Layer Security (TLS): SSL and
TLS are used extensively in the security of online retailers and service providers.
These protocols operate using a handshake method. As IBM explains, "A HTTPbased
SSL connection is always initiated by the client using a URL starting with
https:// instead of with http://. At the beginning of an SSL session, an SSL
handshake is performed. This handshake produces the cryptographic
parameters of the session." These parameters, typically digital certificates, are
the means by which the two systems exchange encryption keys, authenticate the
session, and create the secure connection.
- Point-to-Point Tunneling Protocol (PPTP): PPTP is a ubiquitous VPN protocol
used since the mid-1990s and can be installed on a huge variety of operating
systems has been around since the days of Windows 95. But, like L2TP, PPTP
doesn't do encryption; it simply tunnels and encapsulates the data packet.
Instead, a secondary protocol such as GRE or TCP has to be used as well to
handle the encryption. And while the level of security PPTP provides has been eclipsed by new methods, the protocol remains a strong one, albeit not the most
secure.
- Secure Shell (SSH): SSH creates both the VPN tunnel and the encryption that
protects it. This allows users to transfer information unsecured data by routing
the traffic from remote fileservers through an encrypted channel. The data itself
isn't encrypted but the channel it’s moving through is. SSH connections are
created by the SSH client, which forwards traffic from a local port one on the
remote server. All data between the two ends of the tunnel flow through these
specified ports.
These SSH tunnels are the primary means of subverting the government content filters
described earlier. For example, if the filter prohibits access to TCP port 80, which
handles HTTP, all user access to the Internet is cut off. However, by using SSH, the
user can forward traffic from port 80 to another on the local machine which will still
connect to the remote server's port 80. So as long as the remote server allows outgoing
connections, the bypass will work. SSH also allows protocols that would otherwise be
blocked by the firewall, say those for torrenting, to get past the wall by "wrapping"
themselves in the skin of a protocol that the firewall does allow.
To actually create the VPN tunnel, the local machine needs to be running a VPN
client. Open VPN is a popular—and free—multi-platform application, as is LogMeIn
Hamachi. Windows users also have the option of using the native OS VPN client.
So whether you're a cubicle monkey, file pirate, or just don't want The Man getting all
grabby with your personal data, virtual private networks are the best means of securing
traffic short of copying it to a flash drive and driving there yourself.